Introduction To Operational Risk And Resilience
Instructor Micky Midha
Updated On Learning Objectives
- Describe an operational risk management framework and assess the types of risks that can fall within the scope of such a framework.
- Describe the seven Basel II event risk categories and identify examples of operational risk events in each category.
- Explain the characteristics of operational risk exposures and operational loss events, and challenges that can arise in managing operational risk due to these characteristics.
- Describe operational resilience, identify the elements of an operational resilience framework, and summarize regulatory expectations for operational resilience.
- Video Lecture
- |
- PDFs
- |
- List of chapters
Chapter Contents
- Definition And Scope Of Operational Risk
- ORM Frameworks And Types Of Risks
- ORM, NFRM and ERM
- Operational Risk Categories
- Legal, Strategic, And Reputational Risks
- Legal Risk And Compliance
- Reputational Risks
- Strategic Risks
- Development Of ORM Frameworks
- ORM Frameworks
- Development Of ORM Frameworks
- Nature And Features Of Operational Risk
- Operational Resilience – Executive Summary
- Operational Resilience
- Operational Resilience And UK Regulations
- BCBS Principles On Operational Resilience
- Operational Resilience And Other Regulators
Definition And Scope Of Operational Risk
- There are many ways operational risk can be defined. It is sometimes defined very broadly as any risk that is not a market risk or credit risk. A much narrower definition is that – it consists of risks arising from operational mistakes, including the risk that a bank transaction is processed incorrectly, but excluding the risk of fraud, cyberattacks, or damage to physical assets.
- Operational risk has been defined by the Basel Committee as –
“The risk of loss resulting from inadequate or failed internal processes, people, and systems or from external events.” - The International Association of Insurance Supervisors defines operational risk similarly as – “The risk of adverse change in the value of capital resources resulting from operational events such as inadequacy or failure of internal systems, personnel, procedures or controls, as well as external events.”
- These definitions include the risks arising from computer hacking, fines from regulatory agencies, litigation, rogue traders, terrorism, systems failures, and so on. However, they do not include strategic risks or reputational risks.
ORM Frameworks And Types Of Risks
- A risk management framework is a representation of actions, techniques, or tools deployed to manage an entity’s risks.
- An operational risk management framework (ORMF) is structure for managing the risks associated with elements of operational risk. The identification, assessment, monitoring, and reporting of risks to which an organisation may be currently or potentially exposed is a primary goal of an operational risk management framework (ORMF). This framework should have explicit policies, protocols, and procedures for
- detecting potential operational risks,
- evaluating the seriousness of those risks, and
- creating plans to managing those risks.
- A wide range of potential risks have to be managed by the ORMF, such as inadequate systems, poor protocols or technology, human errors, cyberattacks, financial losses from fraud or theft, reputational harm from regulatory infractions, and even natural disasters. The ORMF must have a comprehensive strategy that considers all facets of business operations in order to properly manage these risks.
ORM, NFRM and ERM
- Another name sometimes used for operational risk in banking, is a non-financial risk (NFR). Some banks may not have an ORM department, but an NFRM department. The name refers to the causes of operational risk, not its consequences, which can be financial, operational, or both. However, unlike market risk and liquidity risk – and credit risk to some extent – the drivers of operational risk are typically non-financial in nature.
- ERM refers to the holistic management of all a firm’s risks.
- In the financial sector, market and credit risks are extremely important, and ERM provides a framework for managing these financial risks as well as non-financial risks from a firm- wide perspective.
- However, in some industries outside the financial sector such as health care and technology, a firm’s risk exposure can be dominated by operational risks. In these instances, there may be little difference between ERM and ORM.
Operational Risk Categories
- Basel II provides seven “Level 1” categories based on loss events.
- Each Level 1 category is divided into Level 2 sub-categories
- Each Level 2 sub-category is broken down into Level 3 activity examples.
- The table in the next page presents the seven level 1 categories, their common acronyms, and high-level examples. The proportions of frequency and severity per event type are calculated from bank operational loss data for 2014 to 2019 and can be considered representative of the industry.
- The full categorization comprises the Basel taxonomy for operational risk which will presented in full in a later chapter.
- The modeling of loss event data differs for each Basel II event risk category, depending on the characteristics and severity of the events within each category.
Sr. No Event Type Acronym Examples Metrics Frequency Severity 1 Internal fraud IF Fraud and unauthorized activities by employees 2% 2% 2 External fraud EF Theft and fraud, hacking damage 30% 9% 3 Employment practices and workplace safety EWPS Contract termination issues, discrimination, employer’s liability 15% 5% 4 Clients, products, and business practices CPBP Client misinformation, complaints, and discounts due to errors, product misspecification 22% 52% 5 Damage to physical assets DPA Destruction of equipment, natural disasters, losses 1% 1% 6 Business disruption and system failures BDSF IT breakdown, outages 2% 5% 7 Execution, delivery, and process management EDPM Processing errors, missing documentation, vendor disputes 28% 27%
- Analysis of frequency versus severity per event type reveals the relative severity of events.
- For example, external fraud, is overrepresented in frequency (30%) versus severity (9%), indicating that many external fraud incidents are relatively small. Indeed, banks collect thousands of credit card fraud incidents every month, sometimes many more for very large retail banks, and most of them are quite small.
- Conversely, the CPBP category constitutes more than half (52%) of the operational losses, from less than one-quarter of event frequency (22%). The inclusion in this category of fines imposed on banks by regulators – sometimes amounting to billions of dollars – explain this imbalance.
- Overall, 75% of the frequency of operational risk events are concentrated in four categories – EF, EPWS, CPBP, and EDPM.
- Only two event types – CPBP and EDPM – are enough to explain 79% of the severity.
- These numbers capture only the direct financial losses associated with each operational risk incident. The indirect consequences of large operational risk events such as reputational damage, drop in market capitalization, management turnover, and remediation costs sometimes far exceed the direct financial cost.
Legal, Strategic, And Reputational Risks
- The BCBS definition of operational risk has a complement that reads –
This definition includes legal risk, but excludes strategic and reputational risk. - The Basel Committee on Banking Supervision (BCBS) has sparked discussions and speculations among experts due to its decision to include legal risk while excluding strategic and reputational risk.
- However, BCBS recently altered its position by stating, in its latest Revisions to the Principles for the Sound Management of Operational Risk (RPSMOR) published in 2021, “Where appropriate, strategic and reputational risks should be considered by banks’ operational risk management.”
Legal Risk And Compliance
- Legal risk pertains to issues related to
- contract enforceability,
- breaches of contracts,
- the applicability of laws and regulations,
- and the potential for financial losses in cases of errors or breaches.
Nearly all operational event categories can be associated with legal risk, but it is more commonly linked to event types 3 (EPWS) and 7 (EDPM).
- Compliance involves adhering to the full spectrum of rules and regulations pertinent to a particular activity, as well as legal requirements. During the early stages of operational risk management, compliance risk was primarily categorized under event type 4 (CPBP). However, over time, regulations within the financial sector have expanded, leading to significantly increased sanctions.
- Many larger banks have established specialized departments dedicated to the management of legal and compliance risk. In some organizations, the compliance department also encompasses operational risk management as one of its core functions
Reputational Risks
- The harm to an organization’s reputation that arises from certain operational incidents is often denoted as reputational risk. In this context, reputational risk is not primarily a direct risk but rather a consequential type of risk.
- Despite the regulator’s exclusion, most financial businesses include reputational harm assessment and management in their ORM efforts. Most impact assessment tables of operational risk cover reputational damage, its prevention, and the response to situations that can cause such damage.
- There are instances where an organization intentionally exposes its reputation to risk for business purposes. For instance, a company may choose to operate in specific regions, offer certain product categories, adopt a controversial marketing strategy to enhance brand recognition, or secure more business, even if these choices carry implications for its reputation and standing with specific stakeholders or interest groups. In such cases, the company must make a deliberate assessment of its risk tolerance, accepting a higher level of reputational risk in exchange for anticipated higher returns.
Strategic Risks
- Strategic risks include the risks connected to decisions made in a wide range of contexts, including –
- mergers and acquisitions,
- large-scale investments,
- forays into untapped markets
- new product categories,
- pricing tactics, etc.
Essentially, strategic risks are the risks of failing to achieve the business objectives with respect to any of these decisions. Hence it is important to align risk management with strategy and business objectives.
- Operational risk is arguably mostly caused by people, who are also its primary means of mitigation. Strategic performance is primarily influenced by the skill of senior management. Strategic risk is actually operational risk in the boardroom due to the significance of people’s competency, the quality of information, and solid governance to a firm’s strategic performance.
Development Of ORM Frameworks
- Because a significant proportion of ERM activities is related to operational risk management in some industries outside the financial sector, financial institutions can take inspiration from ERM frameworks to develop their ORM frameworks (ORMF).
- The most widely adopted ERM frameworks are the
- International Organization for Standardization (ISO) 31000 standards, and
- COSO ERM from the Committee of Sponsoring Organizations.
- UN organizations, for instance, follow the ISO risk management framework. Other public or international organizations such as the World Bank get their inspiration from the COSO model.
- While some risk management framework representations emphasize actions, others emphasize tools and procedures. The diagram in the next page gives an illustration of a representation that links actions to procedures. It is beneficial for businesses to build a comprehensive image of their risk management procedures – one that explains the connections between activities, resources, and methods. Most risk management actions and techniques are represented in the diagram, which any company can customize based on its own procedures.
ORM Frameworks
Risk management cycle: Four actions of risk management.
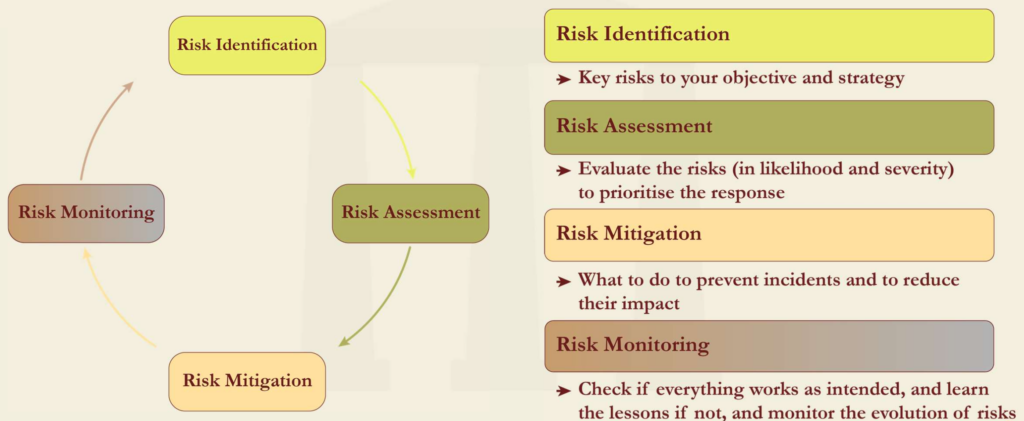
Development Of ORM Frameworks
- The framework offered here includes additional building pieces for
- Risk governance – This relates to the assignment of roles and responsibilities in the organization to execute and report on risk management.
- Risk conduct and culture – These relate to gaining the hearts and minds of everyone in the firm about risk management and good behavior
- Risk appetite – This is considered a main component of an ORM framework because it drives the priorities of risk exposure and risk mitigation.
- This framework is more complete and in line with typical financial sector practice.
Nature And Features Of Operational Risk
| Category | Description |
|---|---|
| Heterogenous | Operational risk is a set of eclectic risks, with different causes, consequences, and distributions of losses. Even within a risk category, operational risk events can be very different. External fraud incidents range from stolen credit cards to ransomware. Internal fraud incidents include cash theft and rogue trading. |
| Idiosyncratic | Operational risk types such as EDPM are driven or mitigated by the quality of a firm’s processes and systems. Others such as DPA are often caused by external events. Largely though, operational risk can be mitigated or elevated by a firm’s ability and willingness to manage it. However, even for very risk-averse organizations, operational risk cannot be entirely eliminated through avoidance, hedging, or insurance. |
| Heavy tailed | Operational risk materializes, for most event types, in a multitude of small losses, and a small number of large losses several orders of magnitude bigger than the median of the distribution. |
| Interconnected | Despite heterogeneity, the different types of operational risk are partially correlated because several of them share common internal causes, such as weaknesses in certain controls, human errors, or poor risk culture; or common external causes, such as economic, political, and environmental events. |
| Dynamic | The nature and intensity of the many operational risk exposures depend on the activities of an organization or industry, and they evolve with these activities. The evolution of operational risk follows the development of the industry itself. |
Operational risk has unique characteristics which make it particularly challenging to manage and complex to model –
- Heterogenous
- Operational risk is quite heterogeneous since it covers a wide range of potential threats, including physical asset damage from natural disasters as well as external fraud in retail transactions like counterfeit currency and forged checks.
- Depending on the type of business line and financial services for which the event occurs, each type of operational risk manifests itself in a different way.
- Also, within each broad group, operational risks can also vary: For example, not all errors or fraud instances are the same.
- The process of thoroughly identifying, defining, and categorizing operational risk into useful taxonomies becomes more challenging due to this heterogeneity.
- Modeling for operational risk assessment is similarly impacted by heterogeneity.
- Idiosyncratic and Diffuse
- Operational risk must be managed by every employee of the company depending on the work at hand because it comes from every person and process in the organisation.
- To prevent fraud and mistakes, back-office staff members must meticulously reconcile transactions before validating them.
- To prevent disruptions or glitches, IT administrators should execute a thorough testing process before to rolling out a new IT application.
- To prevent compounding the net loss in the event of client default, credit officers must properly document the credit collateral.
- Everyone is a risk manager, as the adage goes in ORM. Hence, ORM cannot be centrally managed in in a way credit risk management (CRM) and market risk management (MRM) can be done.
- The central ORM function is crucial to centralizing reporting and information on operational risk, as well as producing guidance for management, but the management of operational risk itself sits with each employee of an organization.
- Heavy Tailed
- Losses from operational risk manifest in a very asymmetric fashion. The operational loss distribution is highly skewed, with the majority of the density of events centered in the lower portion of the distribution, but with a heavy tail extending to a few very big events, several orders of magnitude greater than the median.
- The strong tail of operational loss distribution makes quantification at the highest percentiles extremely uncertain. Typical statistical models may not be able to adequately account for these severe events. Organizations could employ other techniques to handle this problem, such as stress testing or scenario analysis, to assess the potential effects of such events and make plans appropriately.
- Interconnected
- The connection between various risk types is a significant characteristic of operational risk. Operational risk is typically caused by poor controls, prejudices and flaws in human behaviour, and changes in the operating environment. These serve as the common causes of a wide range of risk events, not only in operational risk but also in credit and market risk.
- Risk events that materialise in a different category than they trigger are boundary events. Even if the cause was an operational risk, entering a transaction in the incorrect direction (buying instead of selling or vice versa) is likely to result in market losses. Similar to this, incorrect credit processing can cause the bank to incur credit losses.
- Dynamic
- The nature of operational risk is dynamic and evolving. The evolution of operational risks in the financial industry, for example, follows the development of the financial industry itself. Significant operational risk debates started with the losses generated from excessive exposure and fraudulent trading in the new derivatives markets in the late 1990s. (e.g. failure of Barings Bank in 1996).
- As the sectors and environment have changed, operational hazards have taken on severe shapes. Severe manifestations of DPA include large-scale physical catastrophes like the terrorist acts of September 11, 2001, or the earthquake that resulted in the nuclear accident at the Fukushima facility in Japan.
- When the digitalization of the financial-services industry generalized, the largest operational losses soon related to cyberattacks and other cyber fraud.
- COVID-19 pandemic had profound effects on the organization of work and accelerated digitalization.
Operational Resilience – Executive Summary
- Operational resilience is fundamentally different from traditional business continuity (BC) and disaster recovery (DR) –
- BC and DR have historically been heavily focused on physical events, were designed and tested independently. Also, these two are mainly viewed as a compliance exercise by most organizations.
- Operational resilience, instead, focuses on the adaptability to emerging threats, the dependencies and requirements for providing critical business services end-to-end, and the broader economic as well as firm-specific impact of adverse operational events. It requires a mindset shift in the organization away from resilience as a compliance exercise to resilience as a key organizational capability that is everyone’s responsibility to maintain and continuously improve.
Operational Resilience
- Operational resilience refers to a company’s or the financial industry’s overall capacity to prevent, adapt to, respond to, recover from, and learn from operational disruptions. The regulatory text does not describe resilience in a single line but rather as a collection of factors, such as the following –
- Continuity of business services – By reducing the danger of disrupting essential company functions, this component comes the closest to the traditional method of business continuity planning and prevention.
- Important business services – This is the innovation of the regulatory approach to resilience. The regulators have switched from a continuity perspective based on processes to one focused on services. Companies must determine which services, if interrupted, would result in “intolerable levels of harm to customers or market integrity” and guarantee that these services continue within acceptable tolerances.
- Impact tolerance levels – Amount of disruption that could be tolerated in the case of an incident has to be quantified by the companies. This is similar to the recovery time objective in business continuity planning. The distinction is that resilience must relate to essential business services rather than processes in general. This strategy is justified by the idea that financial service providers must be resilient enough so as not to hurt customers or market integrity in an unacceptably large way. This also helps senior management and the board “set their own standards for operational resilience, prioritize, and make investment decisions.”
- Management of disruption – This includes all actions necessary to reduce any potential negative effects brought on by an unforeseen occurrence or catastrophe. This entails formulating plans that swiftly resume routine business activities while also guaranteeing that service delivery is not significantly disrupted in such circumstances. Strong communication strategies must also be in place in order to keep important stakeholders updated throughout the crisis response procedure..
- Lessons learned – Resilience differs from standard business continuity in a crisis by drawing learning from internal errors or publicly disclosed incidents in other firms. Financial institutions must continually strengthen their resistance to extreme unforeseen shocks by drawing lessons from the past.
- The industry’s thinking has changed toward assuming that major operational interruptions are unavoidable, at least periodically, as a result of the significant rise in cyber risks. Over time, businesses and regulators have shifted their attention from a strictly preventive approach to risk management to a more balanced strategy that considers preventing, identifying, and addressing operational accidents when they happen in order to reduce their total net impact.
- Finally, regulators have made clear that the new requirements will sit alongside existing ORM requirements as opposed to replacing them.
Note – This entire part on operational resilience has been taken from “Building the UK financial sector’s operational resilience”, which is discussed in the next slide.
Operational Resilience And UK Regulations
- UK regulators were the first to publish a consultative paper, then regulatory guidance on resilience.
- The UK Financial Conduct Authority (FCA), Prudential Regulation Authority (PRA), and Bank of England (BoE) have worked toward a comprehensive regulatory framework on operational resilience, which they initiated with a joint discussion paper issued in July 2018 on Building the UK financial sector’s operational resilience.
- In 2018, the BoE stated –
Operational resilience is already a responsibility of firms and FMIs (Financial Market Infrastructure), and an outcome supported by the existing regulatory framework. The supervisory authorities are considering the extent to which they might supplement existing policies to improve the resilience of the system as a whole. - Published in 2018, the UK regulatory paper reads very much like a response to the TSB Bank disruption (see Box 1.2.). At the time, the industry was particularly worried about the risk of IT disruptions and cyberattacks, and built much of their resilience capacity around the continuity of IT infrastructures and services.
- In 2020, the Federal Reserve (Fed) issued its Sound Practices to Strengthen Operational Resilience, along similar lines of important business services, tolerance impact level, and the view of operational resilience as a key outcome of an effective ORMF. The guidance also stresses the need to insert operational resilience in a holistic enterprise management framework. This figure proposes an integrated view of the different risk management activities and departments linked to and supporting operational resilience in financial organizations, composed with the different sections of the Federal Reserve document.
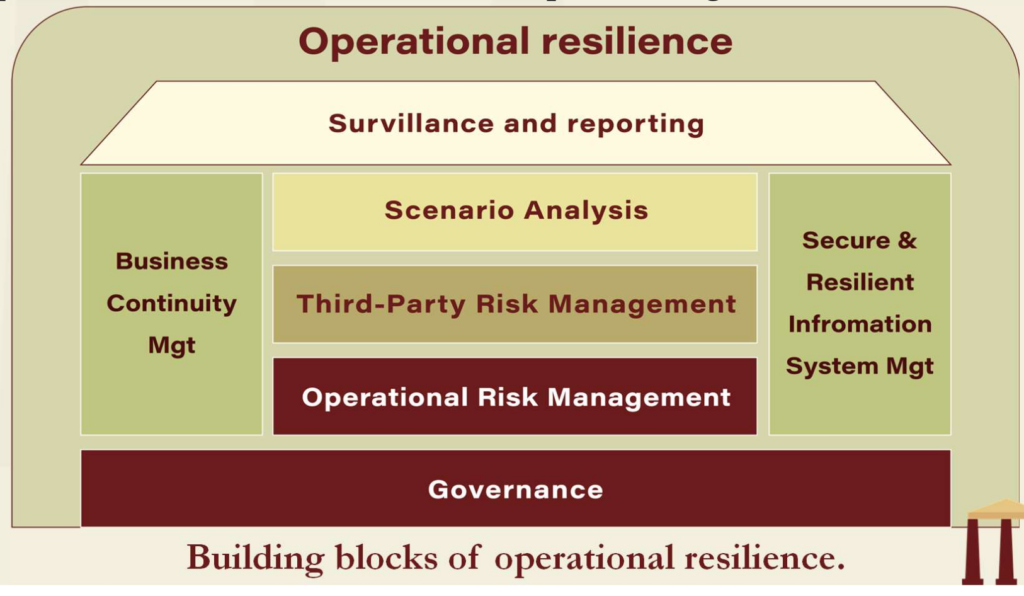
BCBS Principles On Operational Resilience
| Resilience principles category | Banks should… |
|---|---|
| 1. Governance | Utilize their existing governance structure |
| 2. Operational risk management | Leverage their respective functions for the management of operational risk. |
| 3. Business Continuity planning and testing | Have business continuity plans in place. |
| 4. Mapping interconnections and interdependencies | Map the internal and external interconnections and interdependencies that are necessary for the delivery of critical operations. |
| 5. Third party dependency management | Manage their dependencies on relationships, to, third parties or intragroup entities. |
| 6. Incident management | Develop and implement response and recovery plans to manage incidents that could disrupt the delivery of critical operations. |
| 7. ICT including cybersecurity | Ensure resilient ICT including cybersecurity. |
Operational Resilience And Other Regulators
- The UK, US, and BCBS are the three main regulators having issued official guidelines for operational resilience. Other regulators have published consultation documents or guidelines of certain aspects of resilience for firms.
- In September 2020, the European Central Bank (ECB) published a draft regulation of the Digital Operational Resilience Act (DORA) for financial services, as part of a more global strategy of the European Commission to support the development of digital finance in the member countries, while mitigating associated risks. The legislative proposal is due to impose a range of ICT-related requirements on financial entities.
- The Monetary Authority of Singapore (MAS) and The Association of Banks in Singapore jointly issued a paper in early March 2021, Risk Management and Operational Resilience in a Remote Working Environment, which deals with managing new risks that could emerge from extensive remote working arrangements adopted by financial institutions (FIs) amid the COVID-19 pandemic. The risks discussed relate to operations, technology and information security, fraud and staff misconduct, and legal and regulatory risks.





