Learning Objectives
- Explain the Basel regulatory expectations for the governance of an operational risk management framework.
- Describe and compare the roles of different committees and the board of directors in operational risk governance.
- Describe the “three lines of defense” model for operational risk governance and compare roles and responsibilities for each line of defense.
- Explain best practices and regulatory expectations for the development of a risk appetite for operational risk and for a strong risk culture.
- Video Lecture
- |
- PDFs
- |
- List of chapters
Chapter Contents
- Operational Risk In Basel II
- Principles
- Operational Risk Capital
- Expectations Of Regulators
- Roles Of Committees
- Governance And Risk Documentation
- Role Of Board Of Directors
- Three Lines Of Defense
- First Line Of Defense
- Risks Champions And Line 1.5
- Second Line Of Defense
- Third Line Of Defense
- Regulatory Guidance On Risk Appetite
- Risk Appetite Structure And Monitoring
- Risk Appetite Governance
- Risk Culture
Operational Risk In Basel II
The regulation of operational risk was first introduced with the reform of Basel II, first published in June 2004. The regulatory reform introduced three regulatory pillars –
Pillar 1 – Regulatory Capital
- Pillar 1 outlines the methods for calculating the minimum required capital for banks to guard against unexpected losses from credit, market, and operational risks and minimum ratios to control liquidity risks.
Pillar 2 – Supervisory Review Process
- Pillar 2 provides for additional capital needs (referred to as “add-ons”) beyond Pillar 1 capital, based on the unique risk profile of a regulated entity.
Pillar 3: Market Discipline
- Pillar 3 outlines regulations requiring financial institutions to make yearly or quarterly mandatory disclosures of their financial status and risk information.
Principles
The latest Revisions of the Principles for the Sound Management of Operational Risk (RPSMOR) document was published in March 2021. This table presents a high-level view of the principles –
- Culture led by the board of directors and implemented by senior management
- Maintenance of a sound and proportionate ORM framework (ORMF)
- Board review and approval of ORMF
- Risk Appetite and tolerance statement for operational risk to be approved and periodically reviewed by the board
- Senior management role in ORM policies and systems development and implementation.
- Comprehensive identification and assessment of operational risk in material activities
- Change management process adequately resourced and articulated
- Regular monitoring of operational risk profile and exposures
- Strong control environment: internal controls, mitigation, training, and risk-transfer strategies
- Robust information and communication technology (ICT) management program, in line with ORMF
- Business continuity plans in place and linked with ORMF
- Public disclosures on approach to ORM and risk exposures
Operational Risk Capital
- The Basel III regulations were revised in December 2017, eliminating the three-tier system for operational risk capital requirements. The new method, known as the Standardized Measurement Approach (SMA) or Standardized Approach (SA), became effective in January 2023 and will be in effect until January 2025.
From January 2023 – Standardized Approach (SA)
- SA is a slight revision of The Standard Approach (TSA). In SA, the minimum regulatory capital required to cover operational risk, known as operational risk capital (ORC), is calculated as the product of the business indicator component (BIC) and the internal loss multiplier (ILM).
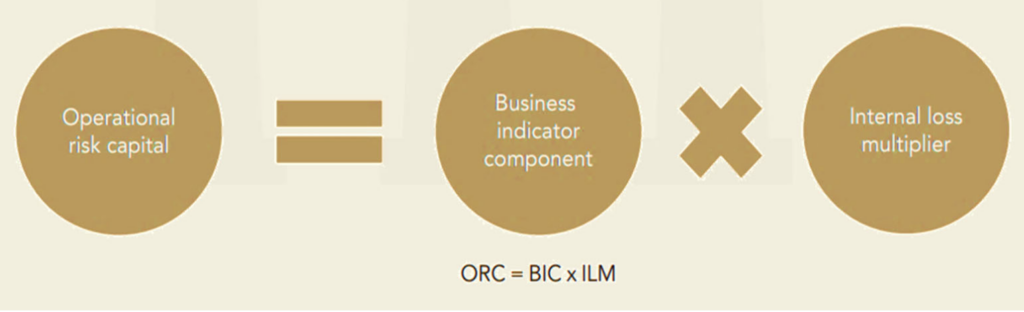
- BIC is a percentage of the bank’s yearly average “business indicator” (BI) over the past three years. BI is the sum of three components (as shown in the previous figure) –
- the interest, leases, and dividends component (ILDC)
- the services component (SC), made of the maximum of fee income and fee expenses, and the maximum of other operating income and the operating expense; and
- the financial component (FC), made of the absolute value of the net profit and loss of the banking book and the trading book.
The marginal weighting percentage \(\alpha_i\) of regulatory capital depends on the size of the business indicator (BI), based on three buckets (𝑖 = 1, 2, 3 denotes the bucket), as given in this table.
BIC = \(\sum \alpha_i \times BI_i\)
| BI Bucket | BI Range | Marginal BI Coefficients (αi) |
|---|---|---|
| 1 | ≤ € 1 bn | 0.12 |
| 2 | € 1 bn < BI ≤ € 30 bn | 0.15 |
| 3 | > € 30 bn | 0.18 |
The regulators seem to have acknowledged that as banks grow larger, the operational risk they face increases at a rate greater than proportionate to their size. To account for this added complexity in processes, operations, and interactions, regulators are increasing the capital requirements. Larger organizations require more funds to cover this extra complexity.
- ILM (Internal Loss Multiplier) is a calculation based on the Business Indicator (BIC) and Loss Component (LC), where LC is determined by multiplying a bank’s average historical losses over the previous 10 years by 15.
ILM = \(\ln \left( e – 1 + \left( \frac{LC}{BIC} \right)^{0.8} \right)\)
ILM = 1 when LC = BIC
ILM > 1 when LC > BIC
ILM < 1 when LC < BIC
Banks with a Loss Component higher than their Business Indicator Component must hold more capital.
- However, this controversial measure has been left to the discretion of the national regulators, and it is possible that most national regulators will simply set the ILM to 1.
Expectations Of Regulators
- The Basel Framework, which encompasses the complete set of standards set by the BCBS, has 29 Core Principles that are essential for effective banking supervision. Among these, several key elements that pertain to the supervision of risk management are –
- a forward-looking assessment of the risk profile,
- establishing strong governance policies and processes to establish
a comprehensive risk management framework, - identifying and managing all material risks according to the firm’s risk tolerance, and maintaining a proper control environment.
Basel Core Principles for Effective Banking Supervision: Abstracts
Principle 8 – Supervisory approach: An effective system of banking supervision requires the supervisor to develop and maintain a forward-looking assessment of the risk profile of individual banks and banking groups, proportionate to their systemic importance;
Principle 14 – The supervisor determines that banks and banking groups have robust corporate governance policies and processes;
Principle 15 – The supervisor determines that banks have a comprehensive risk-management process to identify, measure, evaluate, monitor, report, and control or mitigate all material risks on a timely basis (…).
Principle 25 – The supervisor determines that banks have an adequate operational risk-management framework that takes into account their risk appetite, risk profile and market, and macroeconomic conditions.
Principle 26 – The supervisor determines that banks have adequate internal control frameworks to establish and maintain a properly controlled operating environment for the conduct of their business taking into account their risk profile.
- Supervisors should regularly evaluate a bank’s operational risk management framework (ORMF) by examining its policies, processes, and systems.
- If the evaluation reveals shortcomings, supervisors must take action to ensure the bank addresses them.
- Additionally, supervisors should encourage the bank to continuously improve by monitoring its progress, comparing it with others, and evaluating its future plans.
- Regulators expect operational risk management (ORM) to be more than just a formality of following policies and procedures. Instead, it should be a fundamental aspect of all business decisions and integrated into all operations. To achieve this, employees at all levels should play a role in the decision-making process. Banks must be able to show how decisions are made and that risks are taken into account. This is important for both regulators and auditors.
- When evaluating the implementation of a firm’s operational risk management framework (ORMF), some common questions include –
- Event reports – Are all significant events recorded? Is a thorough analysis performed to identify root causes and glean lessons learned? Are close calls also documented?
- Assessing risks and controls – Is the methodology solid and consistently followed? Are relevant individuals involved in the assessments? Are assessments reviewed and scrutinized by peers to maintain uniformity throughout the organization?
- Risk indicators – Are the values of indicators determined independently? Are the most suitable indicators for their purpose approved by those responsible for managing risk (line managers)? Are they frequently updated?
- Scenarios – Are they comprehensive enough? Are they extreme yet feasible? Is the assessment objective, documented, and capable of being replicated?
- Coverage – Do the reports provide assurance that the scope of ORM for all functions and personnel is comprehensive?
- Risk reporting – Is the data provided adequate for making decisions? Does the information fit the management level to which it is directed?
- Many firms have difficulty showing evidence of their ORM framework due to inadequate documentation and reporting. Regulators consider the lack of evidence to mean that a practice does not exist. Proper documentation is necessary to demonstrate implementation.
Roles Of Committees
- Successful risk governance involves defining the responsibilities of different risk management stakeholders throughout the organization, as well as having a functional decision-making process and enforceable guidelines.
- Risk and Committee Structure
- The governance of operational risk is structured through committee-based, collaborative decision making that is informed by reports and information that is escalated through various levels of a company’s hierarchy. The size and number of committees focused on operational risk governance will depend on the size and complexity of the organization.
- This figure presents an example of a risk committee
structure.

- The larger and more complex firms generally have a pyramid of risk committees with responsibility for the oversight, management, monitoring and reporting (or escalation) of operational risk.
- The lowest level in the operational risk committee structure is usually held by risk committees overseeing activity by business type or location. They are responsible for gathering information to form a comprehensive understanding of the operational risk. They escalate significant concerns to the firm-wide or second line of defense risk committee.
- The task of managing, controlling, and monitoring operational risks has been assigned to the group operational risk committee. This committee reports the consolidated view to the executive risk committee management, management committee and the board risk committee. Creating processes to make sure that all operational activities are carried out in line with applicable laws and corporate policies may also fall under their purview. Additionally, they must regularly provide reports to the executive risk committee management that include an evaluation of the present risk landscape and the efficacy of the measures in place.
- The board-created enterprise-level risk committee (board risk committee) oversees all operational risks. It makes recommendations to the full board with regards to risk -based decisions, risk exposure, and risk management. It reviews and monitors the investigation of larger incidents. To improve the organization’s overall control environment, this committee collaborates closely with senior executives from all divisions. consistent monitoring of operational risks and proper representation and escalation of potential issues to the board. The composition of the board risk committee is governed by guidelines, and regulators require its members to have current and relevant experience.
- The structure and escalation process of a firm’s risk committee typically depend on the size, nature, scale, and complexity of the firm. Smaller firms may have a single operational risk committee that supervises operations and provides reports to the management committee and board risk committee. Different structures may be acceptable if they are justified by the size and complexity of the business.
Governance And Risk Documentation
- The document that outlines the specific powers given to the committee to preside over a designated area of duty is known as the Terms of Reference (TOR) of a committee, or as “a committee charter”. It includes details on the committee’s role and objectives, member names and functions, members’ tasks and responsibilities, meeting frequency, and changes the charter has undergone throughout time along with their justifications.
- The committee discussions, decisions, and reasoning behind these decisions must be documented in committee minutes to demonstrate proper governance of operational risk and comply with regulatory requirements. These requirements apply to other types of risks also.
- Operational policies define a company’s business rules and processes. Procedures and guidelines offer specific guidance on executing tasks, reducing the risk of errors and serving as training tools, especially for new hires. Policies, procedures, and guidelines are a type of internal control called directive controls. Policies and procedures must be widely known, updated regularly, and integrated into the organization’s operations to be effective. They should align with business practices and be relevant, adapting to changes in the business such as new activities or revised processes.
Role Of Board Of Directors
- The board of directors is ultimately responsible for the general administration of the firm, including risk management. The board sets the risk appetite of the firm and makes sure that it operates within the limits of its risk appetite.
- The roles and responsibilities of the board are detailed in Principle 3 of RPSMOR, 2021.
- Regulators demand that the board of directors validate the operational risk management framework, conduct regular revisions, and ensure that senior management effectively implements the policies, processes, and systems of the operational risk management framework at all levels of decision-making.
- The board is also responsible for establishing a risk management culture that is communicated effectively to the firm.
- The board must receive adequate training and make sure that all functions involved in operational risk management receive adequate training in order to effectively carry out their responsibilities. This is necessary for the board to fulfil its responsibility of overseeing operational risk management, which is fully integrated with the rest of ERM
- With new regulations on operational resilience, the duties of the board of a bank or financial institution have been expanded to include monitoring and assurance of the firm’s efficient management of that topic. The board’s obligations for resilience are outlined in Principle 1 of the BCBS, which states that directors must make use of their current governance structure to create, monitor, and implement an efficient operational resilience approach.
- The board of directors should actively participate in creating a general knowledge of the company’s operational resilience approach through clear communication of its objectives.
- The board of directors ensures that adequate financial and technical resources are committed to operational resilience and monitors senior management’s implementation of its operational resilience approach. Senior management should report to the board on a prompt basis and provide assurances of continuous operational resilience, especially where serious flaws could jeopardize the supply of the company’s essential services.
- Companies must be able to show that all staff members receive training on operational resilience obligations and that the board has received this training as well.
Three Lines Of Defense
Over the past ten years, the three lines have evolved into the acknowledged and advised method for structuring controls and risk management in financial services businesses. The three lines often have the following definitions –
- Line 1 – Risk owners are commonly referred to as the first line of defense in a business and include any staff responsible for managing risk, particularly those in front-office positions. The BCBS (RPSMOR) calls this group “business unit management”.
- Line 2 – This group consists of those who independently oversee business operations for risk and ensure that the risk management framework and policies are being applied correctly. They challenge the actions and conduct of the business lines. This second line of defence is referred to by the BCBS (RPSMOR) as “an independent corporate operational risk management function (CORF)”.
- Line 3 – This is the internal audit function. This third level of defence, according to BCBS (RPSMOR), is an “independent assurance”.

- The level of formality in the implementation of the three lines of defense can differ depending on the characteristics of the regulated entity, such as its size, type, and complexity. ORM is typically less centralized than credit, market, or liquidity risks, which makes it more challenging to define the three lines of defence model. Furthermore, control functions, such as finance, legal, or security, may not have a distinct assignment to a specific line of defense within organizations. When it comes to hybrid functions, which are often seen in operational risk across both first and second-line roles, the BCBS requires documenting and clearly defining the first-line and second-line roles. This table gives an example of how first vs second lines of defence roles within hybrid functions could be separated.
| Department | First line role | Second line role |
|---|---|---|
| Legal | Drafting contracts | Overseeing legal activities that take place in the business lines |
| HR | Administering pay, recording performance against objectives | Overseeing people management in the business lines |
| IT Security | Encrypting data, partitioning network, monitoring network activity | Verifying the implementation of ICT controls in the business operations, enforcing security policies |
| Finance | Managing treasury and accounting | Verifying whether business exposures remain under authorized limits |
First Line Of Defense
- The first line of defense, or front-line risk management, typically encompasses all commercial and front-office operations, commonly referred to as “the business”. Risk is managed where it is generated, meaning that it is not owned by the risk management function, but by the business. In defining the first line of defense, it’s better to refer to risk owners rather than the business. Risk owners are responsible for assessing and mitigating the risks they generate or oversee. For example, the head of IT is responsible for IT risk in a firm.
- The following are some duties of an effective first line of defence. –
- Recognizing and evaluating the significance of operational risks that the company faces
- Setting up suitable controls
- Evaluating the layout and performance of these controls
- Monitoring and reporting the operational risk profiles of business units
- The business unit should inform the second line of defense if it feels it does not have sufficient resources, tools, and training to properly identify and evaluate operational risks.
Risks Champions And Line 1.5
- By its very nature, operational risk management is decentralised – it permeates all operations and processes. However, not everyone in the industry has the training necessary to be a risk specialist and comprehend the concepts and jargon of risk management. As a result, many firms assign “risk specialists” or “risk champions” to work with the risk function in each business department. Sometimes referred to as the line “1.5” or “1.b”, these risk experts are also known as “stewards” or “risk correspondents”. They are especially prevalent in bigger enterprises. The following are some of the responsibilities of risk specialists within the first line of defence –
- Being the main correspondent for risk issues
- Collecting and recording the risk events and losses
- Mapping the risks and controls in line with the group definitions (when appropriate)
- Following up on the control rules defined, risk management action plans and audit tracking
- It is important for firms adopting this approach to ensure that the ownership of operational risk in the first line of defense is not assumed by, or passed to, those providing first-line operational specialist expertise and services.
Second Line Of Defense
- This corporate operational risk function (CORF), which is functionally autonomous, establishes the risk management framework and assess its implementation by the first line. They should not directly participate in the risk management tasks carried out by the first line, but rather offer guidance, supervision, and questioning to these tasks.
- Risk professionals in the second line must have expertise in conceptual and technical aspects of risk management, regulatory requirements and business environment. Responsibilities of an effective second line of defense should include the following –
- Establishing and preserving policies, standards, and guidelines for ORM, and providing operational risk training to increase understanding and proficiency in risk management.
- Providing an impartial opinion on the risk management practices used by business units, including their identification of significant operational risks, the design and efficacy of essential controls, and their adherence to risk appetite and tolerance limits. Challenging the business unit’s use of operational risk management tools, measurement activities, and reporting systems for their applicability and consistency, and providing evidence of this productive challenge.
- Reviewing the operational risk profile and contributing to its reporting and monitoring.
- Regulators often require the second line to be “independent” from the first line to offer “oversight and challenge” of risk management activities. But “pure independence” raises the issue of overlap with internal audit and may make it challenging to provide effective oversight before activities are properly implemented, understood, and mature.
- The second line can maintain independence from the first line by providing guidance and asking questions, without influencing the answers.
- For example, a risk manager from the second line may lead a workshop on risk and control self-assessment with staff and managers from a business line, prompting reflections on risks and control effectiveness, while staying neutral by not exercising influence on the content of the answers and assessments made. The manager can then collect the responses and challenge them, while the first line retains the responsibility for final approval.
- The second line is responsible for methodology while the first line owns the risks.
- The level of independence varies among banks. Small banks often achieve independence through separated duties and independent review. Larger banks have an independent reporting structure for the CORF function.
Third Line Of Defense
- Internal audit is the third line of defense and operates independently from the risk management process. It evaluates the control system and compliance with policies and procedures of various departments and activities, including the risk function. Internal audit defines its own view of the organization’s key risks to develop its audit universe.
- The interaction of internal audit with the risk management, compliance, and financial functions is discussed from the perspective of the Institute of Internal Auditors (IIA, 2017) as follows –
- Internal audit should maintain independence from the vital risk management, compliance, and finance functions that form part of an organization’s corporate governance structure. It should not hold any responsibility or affiliation with these functions.
- Internal audit should evaluate the adequacy and effectiveness of risk management, compliance, and finance functions. It should not solely rely on the work of these functions while assessing internal controls and risk management processes. Internal audit should examine a relevant sample of activities being reviewed.
- Internal audit should make an informed decision regarding how much it is appropriate to consider the work done by others in relevant fields, such as risk management, compliance, or finance, when determining whether to take a risk or how much of the activities under review will be subject to audit testing.
- Some institutions prefer to call the 3LoD model “three lines of accountability” to emphasize clear roles and responsibilities across lines and the importance of accountability among actors.
- If a business employs the three lines of defence, it should be aware of the Institute of Internal Auditors’ new Three Lines Model, which was released in 2021. (IIA). In order to promote greater cooperation across business activities, including internal audit, the Institute has improved the model to reflect the development of risk management within enterprises.
- The three lines model highlights the role of expertise and support of the second line, specifically for risk-related matters. The second line should not interfere in business matters outside their area of expertise, which is risk. Some organizations have adopted an independent stance for the risk function, prioritizing oversight and challenge rather than support and expertise. This can lead to confusion with the role of internal audit. The publication from the IIA emphasizes that the second line is part of and reports to general management. This shift moves the approach closer to the models adopted by mature firms in risk management, where risk is seen as a function that helps create and protect value, rather than just controlling and avoiding risk.
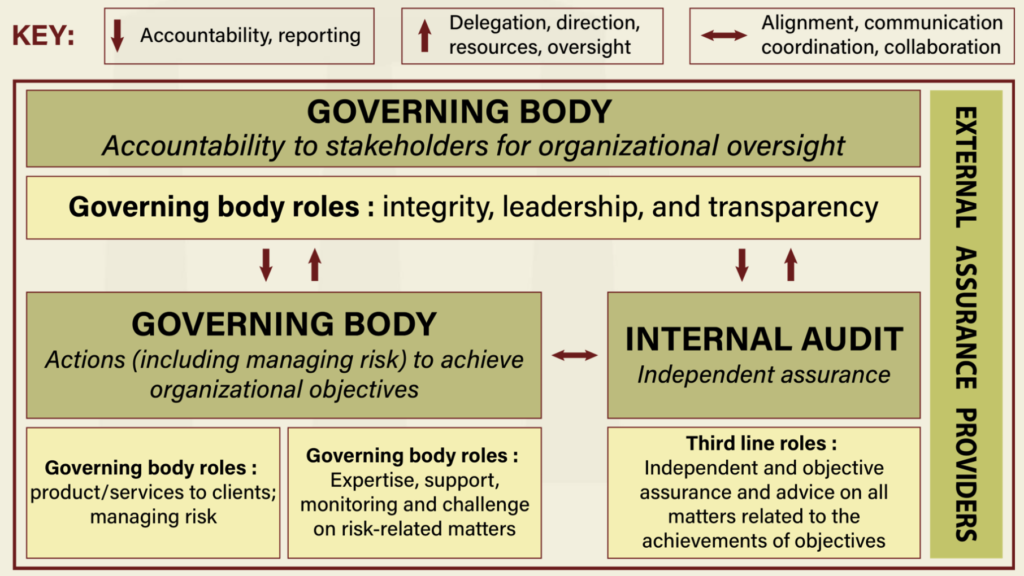
The IIA’s Three Lines Model
Regulatory Guidance On Risk Appetite
- The Board should maintain sound risk management and internal control mechanisms and is responsible for evaluating the kind and scope of important risks it is willing to accept in accomplishing its strategic objectives.
- Risk appetite refers to the assessment of an organization’s key risks, determination of acceptable vs. unacceptable risks, and implementation of controls to limit risk. It can uncover internal contradictions and drive the priorities of the control environment, with ultimate responsibility resting with the board of directors.
- BCBS’s 4th operational risk principle focuses on risk appetite and tolerance. Risk appetite statements need to be easily understood, aligned with the bank’s strategy, monitored through indicators, and forward-looking. Also, they need to justify the reasons for taking, limiting, or avoiding certain types of operational risk They should be subject to scenario and stress testing to ensure they remain within acceptable limits.
- According to Principle 4,
- Approve the bank’s risk appetite and tolerance statements, taking into account all risks and the bank’s strategic direction.
- Regularly review the appropriateness of the statements, considering factors such as changes in the environment, business volumes, risk management effectiveness, loss experience, and limit breaches.
- Regulatory guidance links operational risk appetite and tolerance to limits of risk exposure and requires consistency between these statements and the firm’s operations. For example, a statement of minimal tolerance for data breaches must be supported by strong controls and monitoring measures.
- Ultimately, the board of directors is responsible for maintaining and regularly validating the risk boundaries. In practice, the board frequently assigns this duty to the board risk committee, with support from the risk function to implement the limits through controls and monitor exposure in the business. The risk function also provides regular reports on the same.
Risk Appetite Structure And Monitoring
- According to BCBS, a firm’s motives for taking or avoiding particular kinds of risks should be factored into their risk appetite. Avoiding risk can also cost the firm. The risk-return trade-off must be considered and reflected in the risk appetite statements. The risk appetite statements must align with the firm’s objectives and risk management strategy.
- This figure presents a typical structure of actionable risk appetite and tolerance. A clear and aligned risk appetite is tied to the bank’s strategic objectives and informs decision-making by setting limits on risk exposure, key controls, and incident thresholds. BCBS refers to the metrics used
to monitor these limits as “boundaries or indicators” while banks refer to them as “monitoring Key Risk Indicators (KRIs)”.

- The box in the next page presents a stylized example of a risk appetite and tolerance statement for conducting risk in a sales process with examples of some monitoring metrics.\
| Risk Appetite & Tolerance Conduct | Monitoring Metrics |
|---|---|
| The bank has minimal tolerance for breaches of conduct in its sales process. Complacency with regards to ethics or customer detriment will be immediately and severely sanctioned. Controls and reward structures are designed in such a way that a systematic breach in the sales process, impacting large numbers of customers, is extremely unlikely. However, the bank accepts that, in isolated cases, unintentional mis-selling incidents occur. They need to be quickly addressed and the customer compensated. | Isolated conduct breaches are inevitable in a large retail network employing thousands of agents. The bank accepts the risk if it does not involve more than 0.2% of the sales force and the errors are corrected swiftly. Failing agents will be dismissed if the breach was intentional and will receive remedial training and special monitoring if the breach was unintentional. Affected customers must be fully compensated as soon as the case is identified. Customer complaints must be answered within 24 hours and fully resolved within five working days. |
| KRI | Target |
|---|---|
| % of sales force involved in conduct breaches | ≤0.2% |
| % of customer complaints answered within 24 hours | 95% |
| % of customer complaints resolved within 5 working days | 98% |
Example of Risk Appetite and Monitoring Metrics
Risk Appetite Governance
- For effective governance of risk appetite, it is best to assign a risk owner to each risk type specified in the risk appetite structure. As the risk appetite sub-categories and controls are divided into limits, controls, and monitoring metrics, it is good practice to designate control owners and metrics owners for the various operational risks.
- Control owners are responsible for designing, implementing, and ensuring the effectiveness of controls
- Metrics owners are responsible for collecting, reporting, and monitoring performance metrics related to risk appetite.
- Risk owners, who are responsible for managing, maintaining, and monitoring risks within the specified limits of appetite and tolerance, serve as the front line of risk management and the first line of defense.

Risk Culture
The Importance of Risk Culture for Regulators
- The fact that risk culture is included as the first principle of the BCBS RPSMOR and mentioned in several of the following lines, shows how important the regulatory community views it.
- Risk culture is seen by regulators as being closely related to right conduct and ethics. It should be within the purview of the board, is applied to, and is attested by, all personnel. Events posing a threat to operational risk are less likely to occur in banks with a strong culture of risk management and ethical business conduct, and when they do, they are easier to handle.
- According to Principle 1 – The board of directors should take the lead in establishing a strong risk management culture.which provides appropriate standards and incentives for professional and responsible behavior. It is the responsibility of the board of directors to ensure that a strong operational risk management culture exists throughout the whole organization.
Deploying a Risk Culture Program
- The risk culture must be established by senior management under the direction of the board of directors. This is referred to as “tone at the top” – Senior managers and directors set the tone for the company by their personal conduct as well as through the establishment of expectations and sanctions for employee conduct.
- It is essential for an organization to have a well-documented risk culture that is reflected in policies and codes that are applicable to all members of the organization.
- The establishment of a robust risk culture requires support from management through the reinforcement of codes of conduct and ethics, an appropriate compensation structure, and training programs. It is crucial to design a system for proper risk-taking that requires those taking risks to have a personal stake, and to bear the consequences of their actions. This way, managers and directors who engage in risk-taking activities are held accountable not only for the benefits, but also for any losses that may result from their actions.
- Training programs help build a strong risk culture by raising awareness of operational risks and providing essential risk literacy. Non-financial risk management must be taught and explained, as it may not be intuitive to all.
- Adherence to codes of conduct can be influenced by reinforcement and signaling of discipline. Reinforcement means that rules are taken seriously, but unnecessary blame should be avoided. A “no-blame culture” and a clear “tone from the top” are important for establishing a good risk culture and avoiding blaming those who report issues and incidents. The motto “If you see something, say something” promotes vigilance and escalation, encouraging staff to report risks without fear of retaliation. Whistleblowing remains an effective control for detecting misconduct and fraud.
- The regulatory authority in the UK requires companies to maintain open and transparent communication with regulators and all internal and external stakeholders. Concealing incidents or weaknesses will face consequences if discovered.





